Next Event
幕張メッセ開催Interop Tokyo 2025
- 日程:2025年6月11日(水) - 13日(金)
- 時間:10:00 - 18:00
- 会場:Interop Tokyo 2025
- 小間番号:6F-13
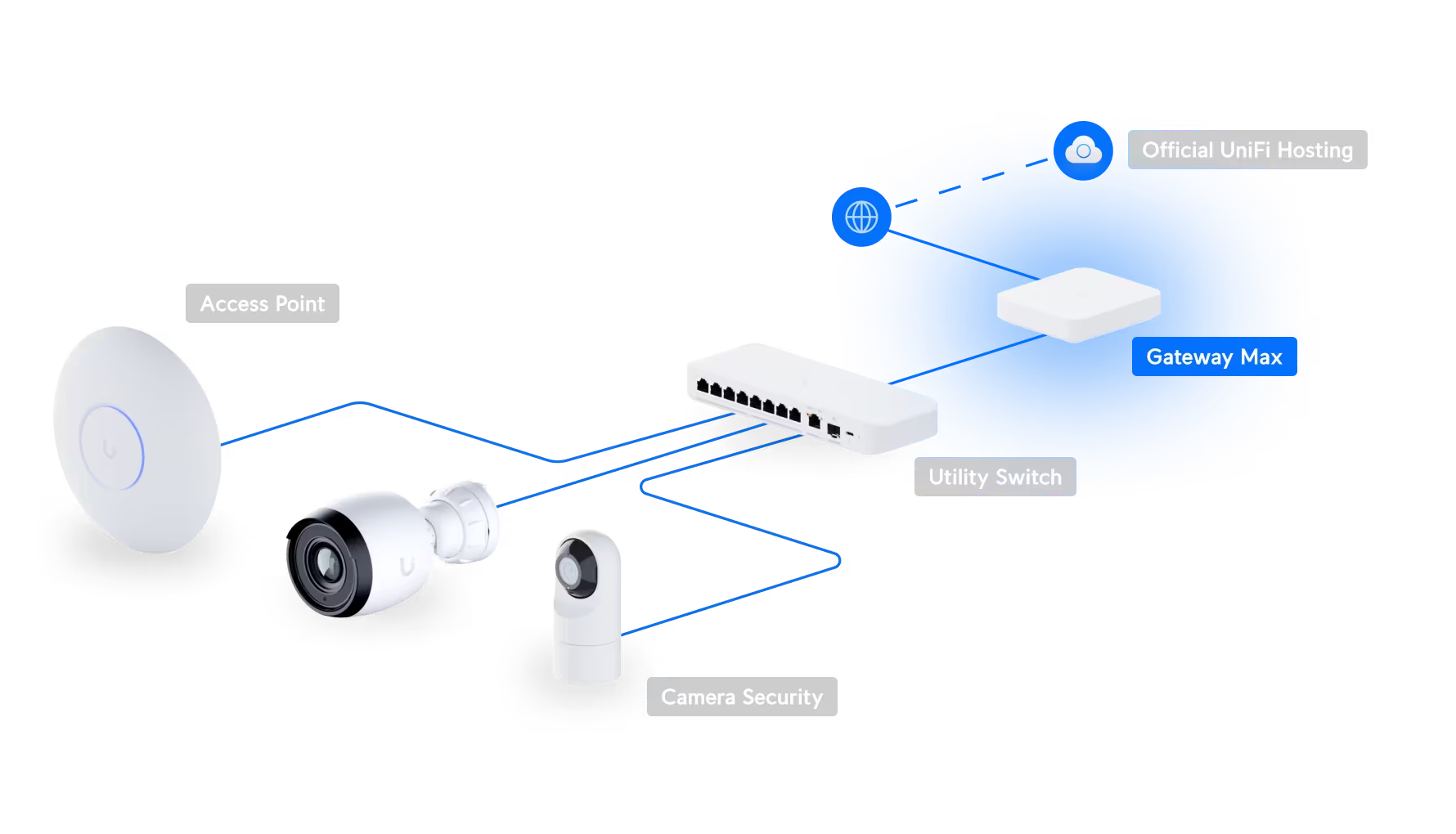
UniFi Live Events
Tokyo Conference
この度、ユビキティ社による UniFi Tokyo Conference
が東京で開催されます。本イベントでは、新製品や今後の展望、導入事例等が紹介される予定です。ネットワークの構築・運用に携わる方にとって、とても有益な内容となっております。
| 日程 | 2026年2月5日(木) |
|---|---|
| 会場 | TKPガーデンシティPREMIUM京橋ANNEX |
| 時間 | 8:30 - 18:00 |
| 08:30 - 09:00 | 受付・デモ展示 |
| 09:00 - 09:05 | 開会挨拶 |
| 09:05 - 09:30 | ITの未来を築く - Building the Future of IT - |
| 09:30 - 10:00 | エンタープライズソリューション |
| 10:00 - 10:30 | MSP / SI の新たな収益創出 |
| 10:30 - 10:45 | コーヒーブレイク |
| 10:45 - 11:45 | 新製品とロードマップ |
| 11:45 - 12:00 | 事例紹介 |
| 12:00 - 12:20 | デザインセンター |
| 12:20 - 12:50 | 製品デモ |
| 12:50 - 12:55 | 抽選会 |
| 12:55 - 13:00 | 閉会挨拶 |
| 13:00 - 14:00 | ランチ |
| 13:00 - 18:00 | エキスパートによる一対一プリセールスセッション |